Security Policy
Brief summary for bug hunters
- Please note that we do not have an established bug bounty program and do not provide rewards for reported issues
- Please note what vulnerabilities are out of scope. Reports that will describe vulnerabilities outside the scope will not be considered.
- When you report the issue to the e-mail specified in the Policy or via our support portal, our security team will be aware of the issue you reported. Due to the high number of out-of-scope / duplicate reports, our security will respond only to the valid, non-duplicate issues reported. Thank you for your understanding.
You can find contact email address for reporting here:
https://tidio.com/security.txt
Disclosure policy
What you can expect from us?
- We will make the best effort that the report will be reviewed in the shortest time, and we will inform you about the priority of the issue and the next steps. (view SLA)
- We won’t report you to authorities for acting in good faith that will help to prepare Proof-of-Concept (view PoC Guidelines)
- If your report will address the issues from the areas mentioned (view Focus Areas) and won’t be a duplicate (or a vulnerability that we are aware of and working on), we will make our best effort to reward you.
- We are not obliged by the law to pay you for every report sent.
What do we expect from you?
- In good faith you will make your best effort not to violate the privacy of our users, destructing or tampering with our data or interrupt the continuity of our services (view PoC Guidelines)
- You will find the vulnerability in our service. Your report will describe it reliably, will be reproducible, and you will be able to provide more information if asked by us.
- You won’t demand payment from us for releasing the vulnerability information to the public – we will gladly reward you if the vulnerability found by you will be unique.
- You will abide by the rules and regulations mentioned on this website (especially What is forbidden).
Process
Service-level agreement
- Time to get a first reply: 2 working days
- Time to prioritize the vulnerability and check it initially: 3 working days
What is forbidden
- Using automated vulnerability scanners (turbo-intruder, fuzzes, etc.), which generate high traffic and put a high load on our infrastructure
- Sociotechnical attacks (phishing, spear-phishing, etc.) on Tidio employees
- Data Exfiltration
- Performing actions that have negative consequences on our service – mass SPAM attack, brute-force or DoS attacks, etc
- Releasing information about vulnerabilities to people not connected to Tidio company
- Using private or sensitive data of our clients for testing purposes
- Testing the vulnerabilities on accounts that you do not own
Scope
The scope defines which resources and what vulnerabilities types and areas are accepted and not in the reports.
Targets
- https://tidio.com/
- https://api-v2.tidio.co/
Exclusions:
- Reports which describes vulnerabilities from the Out-of-Scope list
- Reports describing outdated services without showing a real influence of it in the PoC
- Reports containing highly abstract and theoretical threats without any PoC backup
- Reports containing only results from automated vulnerabilities scanners
- Reports describing vulnerabilities in services used by us, which are 3rd party services.
- Reports describing vulnerabilities possible on outdated web browsers.
Vulnerabilities Out-of-Scope:
- Email Spoofing – incorrect SPF/DKIM/DMARC configuration
- Clickjacking: X-Frame-Options – Vulnerability, which utilizes a lack of proper header, which allows displaying Tidio in an iframe in a different domain
- DoS Attacks
- Lack of a security flag – HttpOnly, Secure
- Lack of security headers – without showing a potential influence on the security
- Brute-force attacks
- Self-XSS – running JavaScript code in your project
- HTML Injection – injecting HTML code into contact forms etc
- CSV Injection – placing executable commands or macros in an imported CSV file that, after exporting, might run harmful code on the computer that it is downloaded onto
- Using weak SSL ciphers
- Lack of CAPTCHA
Focus areas (In-Scope):
- RCE / Command Injection
- SQL Injection
- XSS – stored, reflected, DOM-based
- SSRF
- IDOR / BOLA
- Authorization/Authentication weaknesses – which can lead to taking over an account
- Open redirect
- Information disclosure – only in case of sensitive data
- Local file inclusion / Remote file inclusion
- Business logic flaws / Privilege escalation
Proof-of-Concept
DO NOT escalate any spotted vulnerability while crafting PoC or testing. Please follow the “keep it simple stupid” rule. Examples below:
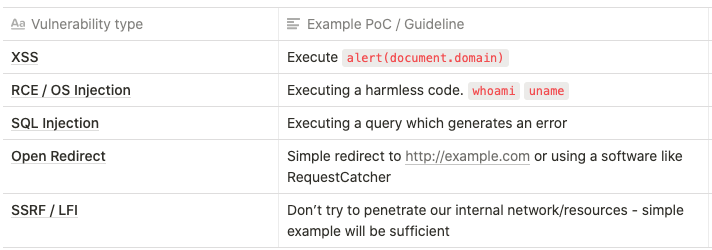
Report guidelines
You should not try to determine the priority in your report because it is business-specific property.
Reports without clear steps for reproduction will not be considered.
We do not have strict rules on how the reports you send should look. Please remember that the report should contain data that will let us reproduce the vulnerabilities and understand the potential threat of it.
Thank you for helping us keep Tidio and our users safe!